Android Users Beware: Malicious Apps Turn Devices into Cybercriminal Proxies
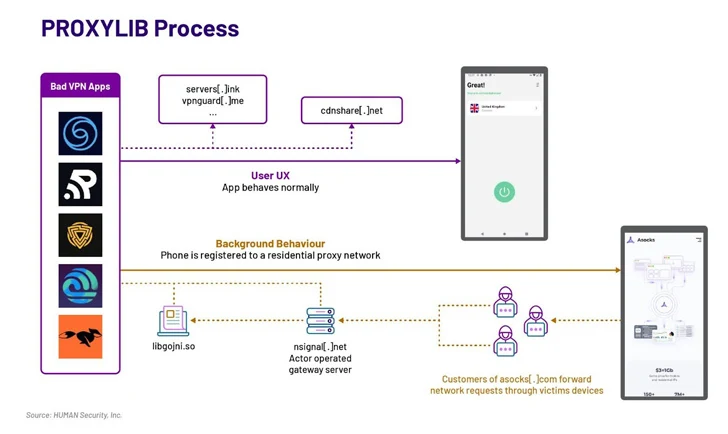
Android users, beware! A recent discovery by HUMAN’s Satori Threat Intelligence team has exposed a cunning scheme involving malicious apps secretly transforming Android phones into proxies for cybercriminals. Codenamed PROXYLIB, this operation involved a cluster of seemingly innocuous VPN apps that harbored a hidden agenda.
The Deceptive Disguise: Malicious Apps Posing as VPNs
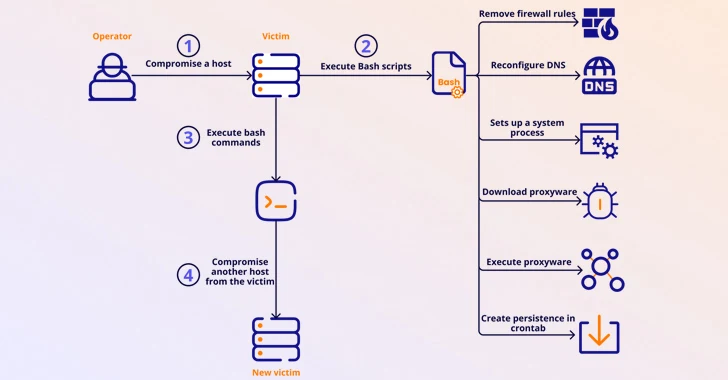
The malicious apps in question appeared on the Google Play Store disguised as legitimate VPN (Virtual Private Network) applications. These apps likely promised features like enhanced privacy or secure browsing. However, unbeknownst to unsuspecting users, the apps were equipped with a malicious Golang library.
Golang Library: The Secret Weapon Behind the Proxy Scheme
The embedded Golang library acted as the silent manipulator. This library, without the user’s knowledge or consent, transformed the infected device into a proxy node within a network controlled by cybercriminals. In essence, the user’s phone became a tool for criminals to anonymously route their internet traffic.
The Purpose of the Proxy Network: Aiding Criminal Activity
The cybercriminals behind PROXYLIB likely aimed to exploit this network of compromised devices for various malicious purposes. Some potential uses of such a proxy network include:
- Scraping data: Criminals could use the network to anonymously scrape data from websites, potentially for illegal activities like identity theft or market research.
- Bypassing geo-restrictions: The network could be used to access content restricted in certain regions, facilitating illegal downloads or copyright infringement.
- Launching cyberattacks: The anonymity provided by the proxy network could be used to mask the origin of cyberattacks, making them harder to trace back to the source.
Extent of the Threat: How Many Apps Were Involved?
While the exact number of downloaded apps is unclear, reports indicate that at least 29 malicious apps were identified and subsequently removed by Google from the Play Store. This incident highlights the constant vigilance required to stay safe in the digital world.
Protecting Yourself: How to Stay Safe from Proxy Malware
Here are some crucial steps Android users can take to safeguard themselves from falling victim to similar schemes:
- Download apps only from trusted sources: Stick to the official Google Play Store and avoid downloading apps from unofficial third-party stores.
- Scrutinize app permissions: Pay close attention to the permissions an app requests during installation. Be wary of apps asking for unnecessary permissions not relevant to their advertised functionality.
- Read reviews and ratings: Checking user reviews and ratings can sometimes reveal red flags about an app’s legitimacy.
- Install a reputable security app: Consider installing a robust mobile security app that can detect and prevent malware infections.
This incident underscores the importance of user awareness and responsible app selection practices. By staying informed and exercising caution, Android users can protect themselves from falling prey to such malicious tactics.
You think you have a story worth everyone’s time? SUBMIT A STORY and we will publish it.
Share this content:




Post Comment