Gamers Beware: New RedLine Stealer Variant Hides in Game Cheats

Gamers, watch out! A new devious variant of the notorious RedLine Stealer malware has been discovered. This iteration cleverly disguises itself as game cheats, tricking unsuspecting players into installing it on their devices.
McAfee Labs, a cybersecurity firm, unearthed this information stealer. The malware leverages Lua bytecode, a scripting language, to enhance its stealth and make detection more challenging.
RedLine Stealer: A Notorious Threat
First documented in 2020, RedLine Stealer has become a persistent menace. It’s typically delivered through various means like email phishing campaigns, malvertising, or even exploit kits and loader malware like dotRunpeX and HijackLoader.
This malware acts like a digital vacuum cleaner, siphoning sensitive information from your device. Its targets include:
- Cryptocurrency wallets
- VPN software
- Web browsers (login credentials, autocomplete data, credit card information)
- IP addresses (revealing your geolocation)
Disguised as a Friend, Acting Like a Foe
What makes this new variant particularly troublesome is its use of game cheats as a disguise. Gamers frequently seek out these enhancements to improve their gameplay. However, in this instance, downloading the malicious software can leave them vulnerable to data theft.
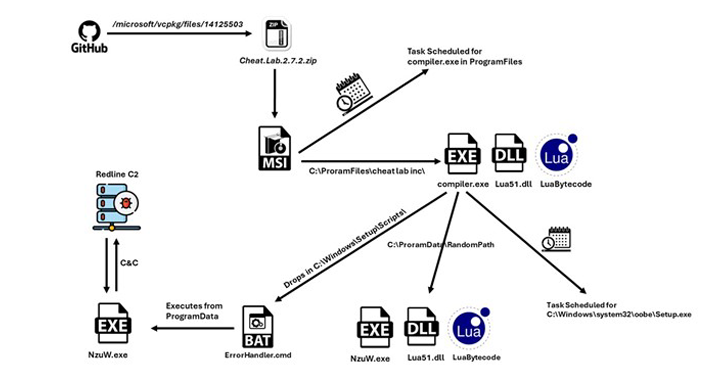
RedLine Stealer isn’t new, but it’s become a popular tool for cybercriminals due to its versatility. This particular variant highlight a concerning trend: leveraging trusted platforms to spread malware. The attackers cleverly uploaded the malicious payload, disguised as ZIP archives named “Cheat.Lab.2.7.2.zip” and “Cheater.Pro.1.6.0.zip,” to two of Microsoft’s official repositories for the C++ Standard Library (STL) and vcpkg. This tactic exploits the trust users have in these repositories, making it more likely victims will download the infected files.
The ZIP files masquerade as game cheats, further solidifying the target audience. Once downloaded, an MSI installer unfolds, designed to execute malicious Lua bytecode. This scripting language makes it harder for security software to detect the threat. The installer even tries to trick the victim into spreading the malware by urging them to share it with friends to unlock the full version.
The malicious code then establishes persistence on the infected system by creating a scheduled task and dropping a command file. This file ultimately launches an executable that communicates with a command-and-control server, effectively turning the infected machine into a backdoor for the attackers. They can then issue commands to steal information like screenshots and send it back to their server.
The “compiler.exe” executable within the installer, upon running the Lua bytecode embedded within the “readme.txt” file present in the ZIP archive, sets up persistence on the host using a scheduled task and drops a CMD file, which, in turn, runs “compiler.exe” under another name “NzUw.exe.”
In the final stage, “NzUw.exe” initiates communications with a command-and-control (C2) server over HTTP, the aforementioned IP address attributed to RedLine.
The malware functions more like a backdoor, carrying out tasks fetched from the C2 server (e.g., taking screenshots) and exfiltrating the results back to it.
The exact method by which the links to the ZIP archives are distributed is presently unknown. Earlier this month, Checkmarx revealed how threat actors are taking advantage of GitHub’s search functionality to trick unsuspecting users into downloading malware-laden repositories.
Protecting Yourself from This Deceptive Attack
Here are some crucial steps you can take to stay safe:
- Download game cheats only from trusted sources: Be wary of unofficial websites or forums offering cheats. Stick to reputable sources endorsed by the gaming community.
- Be cautious of unsolicited offers: If you receive an email or message promoting game cheats, don’t click on any links or attachments. It’s likely a phishing attempt.
- Use robust antivirus and anti-malware software: Security software can help detect and block malware before it infects your device.
- Stay informed: Keep yourself updated on the latest cybersecurity threats. This way, you’ll be better prepared to recognize and avoid them.
In conclusion, gamers and businesses alike need to be vigilant. Stick to official sources for game mods and cheats, use reputable antivirus software, and be wary of anything that seems too good to be true. By staying informed and practicing safe online habits, you can help protect yourself from these evolving cyber threats.
You think you have a story worth everyone’s time? SUBMIT A STORY and we will publish it.
Share this content:




Post Comment