Dark Web and Everything about it!
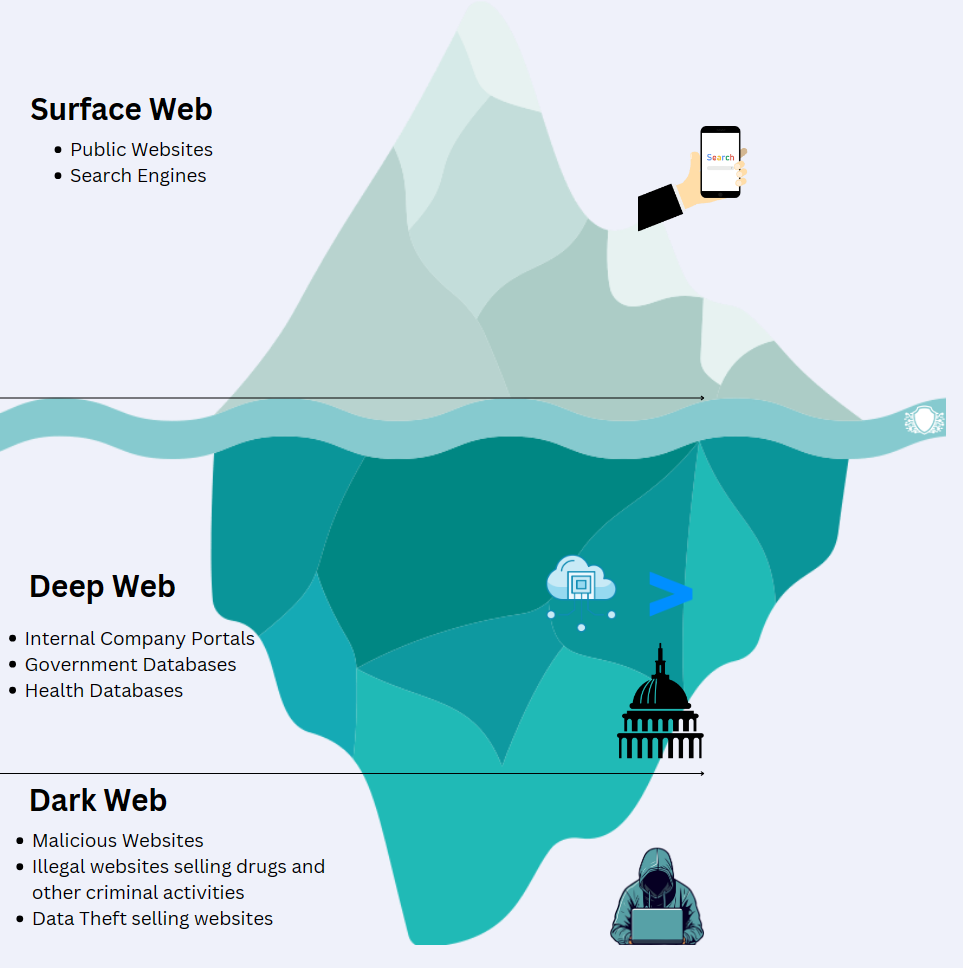
The internet, often likened to an iceberg, has multiple layers, each with its own characteristics and implications. This comprehensive article aims to unveil the secrets of the Dark Web, providing insights into its structure, activities, and the imminent threats it poses to cybersecurity. To fully grasp the Dark Web, it’s crucial to understand its counterparts: the Surface Web, Deep Web, and the statistical landscape that defines their scale.
The Layers of the Internet
1. Surface Web
- Definition: The visible layer of the internet accessible through standard search engines like Google and Bing.
- Characteristics: Publicly accessible, indexed by search engines, and primarily consists of websites intended for the general public.
- Statistics: Approximately 4% of the entire internet constitutes the Surface Web, hosting content ranging from informational websites to e-commerce platforms.
2. Deep Web
- Definition: The concealed layer of the internet not indexed by traditional search engines.
- Characteristics: Requires specific access credentials or direct URLs, hosting databases, academic records, and other non-indexed content.
- Statistics: Estimated to be 90-96% of the entire internet, the Deep Web encompasses a vast array of information beyond the reach of search engine crawlers.
3. Dark Web
- Definition: A subset of the Deep Web intentionally hidden, requiring specialized software such as Tor for access.
- Characteristics: Home to encrypted websites and marketplaces, facilitating anonymous and often illicit activities.
- Statistics: While precise measurements are challenging, the Dark Web is a fraction of the Deep Web, representing a concealed space for various cyber threats.
Unmasking the Dark Web
Access Mechanisms:
- The Role of Tor (The Onion Router):
- Encryption and Anonymity: The Dark Web relies heavily on Tor, a specialized browser that enables anonymous access by encrypting users’ internet traffic and bouncing it through a series of volunteer-operated servers.
- Layered Routing: Tor uses a layered routing approach, encrypting data in layers like an onion, hence the name. This obscures the source and destination of the data, ensuring a high level of anonymity.
- Hidden Services (.onion domains):
- Unique Domain Structure: Websites on the Dark Web often use “.onion” domains, which are not indexed by traditional search engines. These domains can only be accessed through the Tor browser.
- Decentralized Hosting: Dark Web sites are hosted on a decentralized network of servers, contributing to the resilience and difficulty in tracking.
Cryptocurrencies:
- Bitcoin Dominance:
- Pseudonymous Transactions:
- Bitcoin’s Pseudonymous Nature: Bitcoin transactions operate on pseudonyms, with users identified by their wallet addresses rather than personal information.
- Widest Acceptance: Bitcoin’s pseudonymity makes it the most widely accepted cryptocurrency on the Dark Web, facilitating transactions without revealing real-world identities.
- User Anonymity Challenges: While pseudonymous, transaction patterns and addresses can be analyzed, posing challenges to complete anonymity.
- Decentralization:
- Decentralized Blockchain: Bitcoin operates on a decentralized blockchain, distributed across a network of nodes globally.
- Alignment with Dark Web Ethos: Bitcoin’s decentralized nature aligns with the ethos of the Dark Web, where a lack of central authority fosters anonymity.
- Resilience and Anonymity: Decentralization enhances the resilience of Bitcoin and contributes to the anonymity of Dark Web users.
- Pseudonymous Transactions:
- Monero for Enhanced Privacy:
- Privacy-Focused: Monero, another cryptocurrency, is gaining popularity for its enhanced privacy features. It utilizes advanced cryptographic techniques to ensure transaction unlinkability and untraceability.
- Fungibility: Monero’s focus on privacy makes it a preferred choice for transactions where users seek maximum fungibility and anonymity.
Unmasking the Dark Web involves navigating the intricate web of access mechanisms and the utilization of cryptocurrencies. While these technologies provide anonymity, they also present challenges for security professionals and law enforcement in their efforts to combat cybercrime on the Dark Web.
Unveiling Illicit Trade and Collaborative Cybercrime on the Dark Web
Illicit Trade:
Drugs:
- Availability: Dark Web marketplaces facilitate the trade of various illicit substances, providing users with a platform to purchase drugs anonymously.
- Cryptocurrency Transactions: Transactions predominantly occur through cryptocurrencies, adding a layer of anonymity for both buyers and sellers.
- Law Enforcement Challenges: Monitoring and combating the illegal drug trade on the Dark Web present substantial challenges for law enforcement agencies globally.
Stolen Data:
- Data Breach Commodification: Illicit platforms offer stolen data, including personal information, login credentials, and financial details, obtained through data breaches.
- Financial Transactions: Cybercriminals trade in stolen data using cryptocurrencies, making it difficult to trace and mitigate the impact on affected individuals.
- Identity Theft and Fraud: Purchased data fuels identity theft and financial fraud, contributing to the escalation of cyber threats.
Hacking Tools:
- Market for Exploits: Dark Web marketplaces host a variety of hacking tools, exploit kits, and malware for sale.
- Zero-Day Exploits: Cybercriminals leverage the availability of zero-day exploits, which target vulnerabilities unknown to the software vendor.
- Amplifying Cyber Threats: The commodification of hacking tools amplifies the scale and sophistication of cyber threats faced by organizations and individuals.
Collaborative Cybercrime:
Underground Forums:
- Expertise Sharing: Underground forums serve as hubs for cybercriminals to share knowledge, techniques, and experiences.
- Specialized Skills: Collaboration enables individuals with different skills to contribute to cybercrime activities, enhancing overall capabilities.
- Training Grounds: Novice hackers can learn from seasoned counterparts, fostering the growth of a diverse and skilled cybercriminal community.
Illicit Services Exchange:
- Service Offerings: Cybercriminals offer services such as DDoS attacks, ransomware deployment, and hacking-for-hire on underground forums.
- Monetary Transactions: Transactions occur through cryptocurrencies, providing a level of financial privacy for both service providers and clients.
- Cross-Border Collaboration: Collaboration transcends geographical boundaries, allowing cybercriminals to form global networks for more effective and widespread attacks.
Marketplace for Stolen Goods:
- Comprehensive Ecosystem: Underground forums serve as marketplaces not only for hacking tools but also for stolen credentials, compromised accounts, and access to hacked systems.
- Economic Model: Cybercriminals collaborate in a symbiotic economic model, where individuals specialize in different aspects of cybercrime, contributing to the overall success of illicit operations.
- Innovation and Evolution: Collaboration fosters innovation, leading to the continuous evolution of cyber threats and tactics employed by the criminal underworld.
Risks and Mitigations:
Law Enforcement Challenges:
- Coordinated Efforts: Illicit trade and collaborative cybercrime require coordinated efforts from international law enforcement agencies to track, infiltrate, and dismantle criminal networks.
- Technological Solutions: Developing advanced technological solutions for monitoring and preventing illicit activities on the Dark Web is crucial.
- Legislation and Regulation: Strengthening legislation and international cooperation is essential for prosecuting cybercriminals engaging in illicit trade.
Cybersecurity Measures:
- Advanced Threat Detection: Organizations must employ advanced threat detection mechanisms to identify and mitigate cyber threats originating from collaborative cybercrime efforts.
- Employee Training: Awareness programs are vital to educate individuals about the risks associated with illicit trade and the collaborative nature of cybercrime.
Unraveling the complexities of illicit trade and collaborative cybercrime on the Dark Web underscores the persistent challenges faced by cybersecurity professionals and law enforcement agencies. Through concerted efforts, technological advancements, and global collaboration, the battle against cybercriminal networks can be waged more effectively, mitigating the impact of these shadowy activities.
Cybersecurity Challenges and Mitigation Strategies
Cybersecurity Challenges:
Advanced Persistent Threats (APTs):
- Sophistication: APTs are highly sophisticated and targeted attacks often backed by nation-states or organized cybercriminal groups.
- Stealthy Tactics: APTs employ stealthy tactics, residing undetected within networks for extended periods, making them challenging to identify.
- Mitigation: Implementing robust threat intelligence, continuous monitoring, and behavior analytics can help detect and mitigate APTs.
Ransomware:
- Proliferation: Ransomware attacks have surged, targeting individuals, businesses, and critical infrastructure.
- Encryption Tactics: Cybercriminals use advanced encryption techniques, rendering files inaccessible until a ransom is paid.
- Mitigation: Regular backups, employee training, and deploying advanced endpoint protection are critical in preventing and recovering from ransomware attacks.
Insider Threats:
- Malicious and Unintentional: Insider threats can be both malicious (intent to harm) and unintentional (negligence or lack of awareness).
- Data Exfiltration: Insiders may leak sensitive information or unintentionally cause data breaches.
- Mitigation: Implementing strict access controls, conducting regular employee training, and monitoring user behavior can help mitigate insider threats.
Phishing Attacks:
- Social Engineering: Phishing relies on social engineering techniques to deceive individuals into disclosing sensitive information.
- Email and Beyond: Phishing attacks extend to various communication channels, including emails, social media, and messaging platforms.
- Mitigation: Employee awareness programs, advanced email filtering, and multi-factor authentication (MFA) are essential in preventing phishing attacks.
Internet of Things (IoT) Vulnerabilities:
- Proliferation of Devices: The growing number of interconnected IoT devices presents security challenges.
- Weak Security Measures: Many IoT devices have weak security measures, making them susceptible to exploitation.
- Mitigation: Implementing robust IoT security policies, regularly updating firmware, and segregating IoT devices from critical networks can enhance security.
Mitigation Strategies:
Zero Trust Security Model:
- Assume Breach Mentality: Zero Trust assumes that threats may exist both inside and outside the network.
- Micro-Segmentation: Implementing micro-segmentation enhances network segmentation, limiting lateral movement in case of a breach.
- Continuous Authentication: Continuous monitoring and authentication ensure ongoing verification of user identities and device trustworthiness.
Artificial Intelligence (AI) and Machine Learning (ML):
- Threat Detection: AI and ML technologies can analyze vast amounts of data to detect patterns indicative of cyber threats.
- Behavioral Analytics: Implementing behavioral analytics helps identify anomalies and potential security incidents.
- Automation: AI-driven automation aids in real-time threat response and reduces the time to detect and mitigate cyber threats.
Cybersecurity Training and Awareness:
- Employee Education: Regular training sessions and awareness programs educate employees about cybersecurity best practices.
- Simulated Phishing Exercises: Conducting simulated phishing exercises helps employees recognize and resist phishing attempts.
- Cultivating a Security Culture: Fostering a cybersecurity-conscious culture within the organization encourages proactive threat awareness.
Multi-Layered Endpoint Protection:
- Antivirus and Anti-Malware Solutions: Implementing robust antivirus and anti-malware solutions provides an initial defense against various threats.
- Endpoint Detection and Response (EDR): EDR solutions offer real-time monitoring and response capabilities at the endpoint level.
- Application Whitelisting: Restricting the execution of unauthorized applications enhances endpoint security.
Continuous Monitoring and Incident Response:
- Security Information and Event Management (SIEM): SIEM solutions enable continuous monitoring of network activities and log analysis.
- Incident Response Plan: Having a well-defined incident response plan ensures a coordinated and effective response to security incidents.
- Post-Incident Analysis: Conducting thorough post-incident analyses helps identify vulnerabilities and improve future response strategies.
The Future of Dark Web Threats
The future of Dark Web threats is marked by increasing sophistication and diversification of cyber threats. As technology advances, cybercriminals leverage emerging tools and techniques to enhance their capabilities.
Artificial intelligence and machine learning are likely to play a significant role, enabling more targeted and adaptive attacks. The expansion of decentralized technologies, such as blockchain and cryptocurrencies, may further complicate efforts to trace and apprehend threat actors. Additionally, collaborations among cybercriminals on the Dark Web are expected to intensify, forming robust networks capable of orchestrating large-scale, coordinated attacks.
As the threat landscape evolves, cybersecurity professionals face the ongoing challenge of staying ahead of innovative tactics employed by malicious actors operating in the shadows of the Dark Web.
Researchers Accessing the Dark Web
While accessing the Dark Web comes with legal and ethical considerations, cybersecurity researchers often navigate its depths for valuable insights. Here’s how researchers can access the Dark Web responsibly:
- Use Specialized Software: Researchers leverage anonymity tools like Tor to access the Dark Web without revealing their identity.
- Virtual Private Networks (VPNs): A VPN adds an extra layer of security by masking the researcher’s IP address, enhancing anonymity.
- Caution and Legal Compliance: Researchers must navigate the Dark Web responsibly, adhering to legal and ethical guidelines. Engaging in any illicit activities is strictly prohibited.
Conclusion
The Dark Web remains an enigma, harboring sophisticated cyber threats that constantly evolve. Understanding its intricate landscape is imperative for cybersecurity professionals and businesses alike. This article has peeled back the layers, revealing the complexities and challenges posed by the Dark Web. By staying informed, adopting proactive monitoring measures, and fostering international collaboration, the cybersecurity community can strive to mitigate the ever-evolving threats emerging from the shadows of the Dark Web. Stay vigilant, stay secure.
You think you have a story worth everyone’s time? SUBMIT A STORY and we will publish it.
Share this content:




Post Comment