Play Goes After the Core: New Linux Variant Targets VMware ESXi Systems
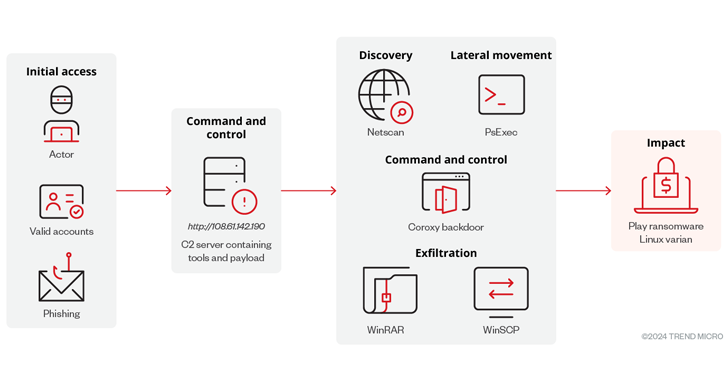
Ransomware continues to evolve, with cybercriminals constantly seeking new ways to exploit vulnerabilities and maximize their impact. A recent discovery by Trend Micro highlights this trend, with the emergence of a new Linux variant of the Play ransomware specifically designed to target VMware ESXi environments.
What is Play Ransomware?
First detected in June 2022, Play ransomware, also known as Balloonfly and PlayCrypt, gained notoriety for its sophisticated tactics. Play utilizes the double-extortion approach, encrypting critical systems and exfiltrating sensitive data before demanding a ransom for decryption. This ransomware has been linked to significant disruptions across various organizations, particularly in Latin America.
Why Target ESXi?
VMware ESXi is a widely used virtualization platform that allows businesses to consolidate multiple virtual machines (VMs) onto a single physical server. This efficiency makes ESXi environments prime targets for ransomware attacks. By compromising a single ESXi server, attackers can encrypt numerous VMs simultaneously, effectively crippling an organization’s core operations and causing substantial data loss.
The New Linux Variant: Broadening the Reach
The newly discovered Linux variant of Play ransomware marks a significant development. Previously, Play primarily targeted Windows systems. This new variant specifically checks for an ESXi environment before executing, indicating a potential shift in the group’s strategy.
Security researchers believe this move suggests a potential expansion of Play’s attacks across the Linux platform. This broader approach could significantly increase the ransomware’s victim pool and potentially lead to more successful ransom negotiations for the attackers.
Technical Details and Potential Impact
While researchers haven’t observed any active infections yet, the Linux variant of Play ransomware exhibits concerning capabilities. The ransomware verifies its environment before proceeding, suggesting a level of sophistication designed to evade detection. Additionally, the variant utilizes the “.PLAY” extension for encrypted files, mirroring the tactics used in Play’s Windows attacks.
The potential impact of this new variant is significant. ESXi environments are the backbone of many organizations’ IT infrastructure. A successful ransomware attack on an ESXi server could result in complete system shutdowns, data loss, and significant financial disruption.
Recommendations and Mitigation Strategies
Here are some crucial steps organizations can take to mitigate the risk of Play ransomware attacks on their ESXi environments:
- Implement strong password policies and enforce multi-factor authentication (MFA) for all ESXi server access.
- Regularly update ESXi software and firmware to patch known vulnerabilities.
- Segment your network to isolate ESXi servers and limit the attack surface.
- Maintain robust backups of your virtual machines and ensure they are regularly tested and secured offline.
- Employ security solutions with ransomware detection capabilities to monitor your environment for suspicious activity.
By following these recommendations and staying vigilant about the evolving ransomware threat landscape, organizations can significantly reduce their risk of falling victim to Play ransomware attacks, regardless of the variant.
You think you have a story worth everyone’s time? SUBMIT A STORY and we will publish it.
Share this content:




Post Comment