RansomHub Group Deploys New EDR-Killing Tool in Latest Cyber Attacks

In a recent development that underscores the evolving tactics of cybercriminals, the RansomHub group has been observed deploying a novel EDR-killing tool in its latest attack campaigns. This new tool, dubbed EDRKillShifter by cybersecurity firm Sophos, is designed to effectively disable endpoint detection and response (EDR) software, a critical layer of defense for organizations.
The Rise of EDR-Killing Tools
The use of EDR-killing tools has become increasingly prevalent among cyberattackers in recent years. These tools are specifically crafted to circumvent EDR systems, allowing threat actors to operate undetected within compromised networks. By disabling EDR, attackers can freely deploy ransomware and other malicious payloads without fear of detection or interruption.
EDRKillShifter: A New Threat
The EDRKillShifter tool, discovered by Sophos during a failed ransomware attack in May 2024, represents a significant advancement in the arsenal of cybercriminals. Unlike previous EDR-killing tools, which often relied on brute-force methods or exploiting known vulnerabilities, EDRKillShifter employs a more sophisticated approach.
How EDRKillShifter Works
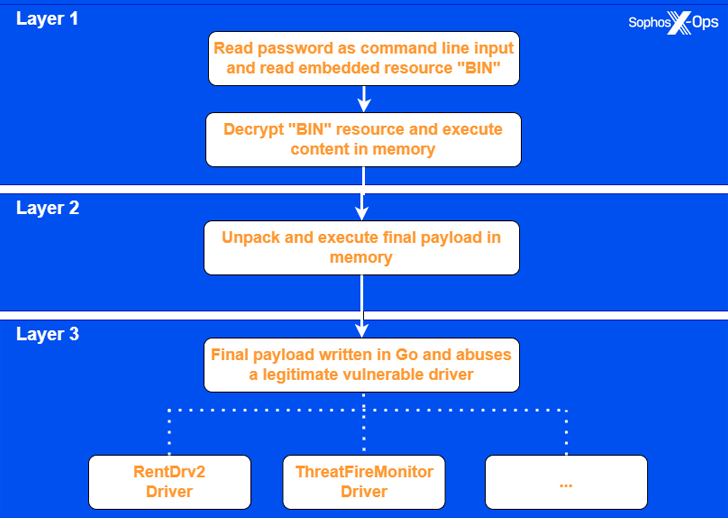
EDRKillShifter functions as a “loader” executable, serving as a delivery mechanism for a legitimate driver that has been compromised. This technique, known as “bring your own vulnerable driver” (BYOVD), allows attackers to leverage existing software components for malicious purposes. The tool can deliver a variety of driver payloads depending on the specific requirements of the attack.
The execution process of EDRKillShifter involves three key steps:
- Loader Execution: The attacker initiates the EDRKillShifter loader on the compromised system.
- Driver Delivery: The loader delivers the malicious driver payload to the system.
- Payload Activation: The driver payload is activated, enabling it to disable EDR functionalities.
Impact and Implications
The deployment of EDRKillShifter by the RansomHub group highlights the urgent need for organizations to strengthen their cybersecurity defenses. By targeting EDR systems, attackers can significantly increase their chances of successful data encryption and extortion.
To mitigate the risks associated with EDR-killing tools, organizations should adopt a layered security approach that includes:
- Regular software updates: Keeping operating systems and applications patched can help prevent exploitation of vulnerabilities.
- Advanced threat protection: Employing advanced threat protection solutions can help detect and block malicious activity.
- Incident response planning: Having a well-defined incident response plan in place can help minimize the impact of a successful attack.
Conclusion
The emergence of EDRKillShifter underscores the ongoing arms race between cybercriminals and defenders. As threat actors continue to refine their tactics, organizations must remain vigilant and adapt their security strategies accordingly. By investing in robust security measures and staying informed about the latest threats, organizations can significantly reduce their risk of falling victim to ransomware and other cyberattacks.
You think you have a story worth everyone’s time? SUBMIT A STORY and we will publish it.
Share this content:




Post Comment