Scams to be aware of in 2024
Scams are nothing new, but they are constantly evolving and adapting to new technologies and human vulnerabilities. Scammers use various methods to trick people into giving them their personal information, money, or access to their devices. They may also use crises, pressure tactics, or fake promises to lure their victims. In this article, we will discuss some of the latest scams that you need to watch out for in 2024, and how you can protect yourself from them.
1. AI-Enabled Scams

Artificial intelligence (AI) is a powerful technology that can be used for good or evil. Unfortunately, scammers are using AI to create more sophisticated and convincing scams that can fool even the most vigilant people. Some examples of AI-enabled scams are:
- AI-powered phishing scams: Phishing is a type of scam where scammers send emails or messages that look like they are from legitimate organizations or individuals, and ask you to click on a link, download an attachment, or provide your personal or financial information. Scammers are using AI to create more realistic and personalized phishing emails or messages, that can bypass spam filters and mimic the writing style or tone of the sender.
- BRC-20 exploits: BRC-20 is a standard for creating tokens on the Binance Smart Chain, a blockchain platform that supports decentralized applications and smart contracts. Scammers are exploiting a vulnerability in the BRC-20 standard, where they can create fake tokens that look like real ones, and trick people into buying them or swapping them with other tokens. The fake tokens are worthless and cannot be transferred or sold.
- Smart contract vulnerabilities: Smart contracts are self-executing agreements that run on a blockchain platform, and can be used for various purposes, such as crowdfunding, voting, or gambling. Scammers are exploiting vulnerabilities in smart contracts, such as bugs, flaws, or loopholes, to steal funds or manipulate the outcome of the contract.
- Deepfake scams: Deepfake technology is a type of AI that can create realistic fake images, videos, or audio of people or events, by using machine learning and deep neural networks. Scammers are using deepfake technology to create fake evidence, blackmail, impersonate, or defame people. For example, scammers can use deepfake technology to create fake videos of celebrities, politicians, or influencers, and use them to spread misinformation, influence opinions, or extort money.
2. Phone Scams

Phone scams are one of the most common and persistent types of scams, where scammers use phone calls or text messages to contact their victims and try to deceive them. Some examples of phone scams are:
- Robocalls: Robocalls are automated phone calls that use a recorded voice to deliver a message or a request. Scammers use robocalls to offer fake products or services, such as auto warranties, vacations, or health insurance, or to issue fake threats, such as lawsuits, arrests, or account suspensions. Some robocalls can even respond to your questions or commands, using AI or voice recognition technology.
- Texts: Texts are short messages that can be sent or received on a phone or a device. Scammers use texts to send fake alerts, notifications, or offers, and ask you to click on a link, download an app, or provide your information. The link or the app may contain malware that can infect your device or steal your data, or the information may be used to commit identity theft or fraud.
- Impersonators: Impersonators are scammers who pretend to be someone else, such as a government official, a law enforcement officer, a survey taker, a relative, a delivery person, or a well-known company. Scammers use impersonation to scare you or gain your trust, and then ask you to provide your information, pay a fee, or buy a gift card. They may also use fake caller IDs, fake documents, or fake websites to make their impersonation more convincing.
- Apps: Apps are software applications that can be installed or accessed on a phone or a device. Scammers use apps to trick you into downloading or using a malicious app that can harm your device or data, or a fake app that can charge you money or steal your information. They may also use apps to access your contacts, messages, or location, and use them to target you or your friends and family.
- QR codes: QR codes are square-shaped barcodes that can be scanned by a phone or a device, and can link to a website, an app, or a payment system. Scammers use QR codes to direct you to a malicious website or app, or to a fake payment system that can charge you money or steal your information. They may also use QR codes to access your device’s camera, microphone, or storage, and use them to spy on you or your activities.
3. Student Loan Forgiveness Scams

Student loan forgiveness scams are a type of scam where scammers target student loan borrowers who are looking for relief from their debt. Scammers use various tactics to deceive borrowers into paying them money or giving them their information, in exchange for false promises of reducing or eliminating their student loan debt. Some examples of student loan forgiveness scams are:
- Application fee scams: Application fee scams are scams where scammers charge borrowers a fee to apply for student loan forgiveness or other debt relief programs. Scammers may claim that the fee is required by the government or the lender, or that the fee is refundable or deductible. However, the fee is actually a scam, and the borrower will not receive any forgiveness or relief. In reality, it costs nothing to apply for student loan forgiveness or other debt relief programs, and the fee is not refundable or deductible.
- Consolidation scams: Consolidation scams are scams where scammers offer to consolidate borrowers’ student loans into a single loan with a lower interest rate or a lower monthly payment. Scammers may claim that they are affiliated with the government or the lender, or that they have access to special deals or programs. However, the consolidation is actually a scam, and the borrower will end up paying more money or losing their benefits. In reality, borrowers can consolidate their federal student loans for free through the U.S. Department of Education, and they should compare the pros and cons of consolidation before doing so.
- Cancellation scams: Cancellation scams are scams where scammers promise to cancel borrowers’ student loans completely, or to negotiate with the government or the lender to reduce or eliminate their debt. Scammers may claim that they have a legal loophole, a secret method, or a special connection that can make this happen. However, the cancellation is actually a scam, and the borrower will not receive any forgiveness or relief.
4. Employment Scams

Employment scams are scams where scammers offer fake or misleading job opportunities to people who are looking for work. They may ask you to pay a fee, provide your personal information, or do some work for free. They may also use fake websites, emails, or phone calls to make their offers seem legitimate.
5. Online Shopping Scams

Online shopping scams are scams where scammers sell fake or defective products, or don’t deliver the products at all. They may use fake websites, social media ads, or emails to lure you into buying their products. They may also ask you to pay with untraceable methods, such as gift cards, wire transfers, or cryptocurrency.
6. Dating and Marriage apps scams

Romance scams are scams where scammers pretend to be interested in a romantic relationship with you, but their real goal is to get your money or personal information. They may use fake profiles, photos, or stories to make you fall in love with them. They may also ask you to send them money for various reasons, such as travel, medical, or legal expenses.
7. Tech Support Scams
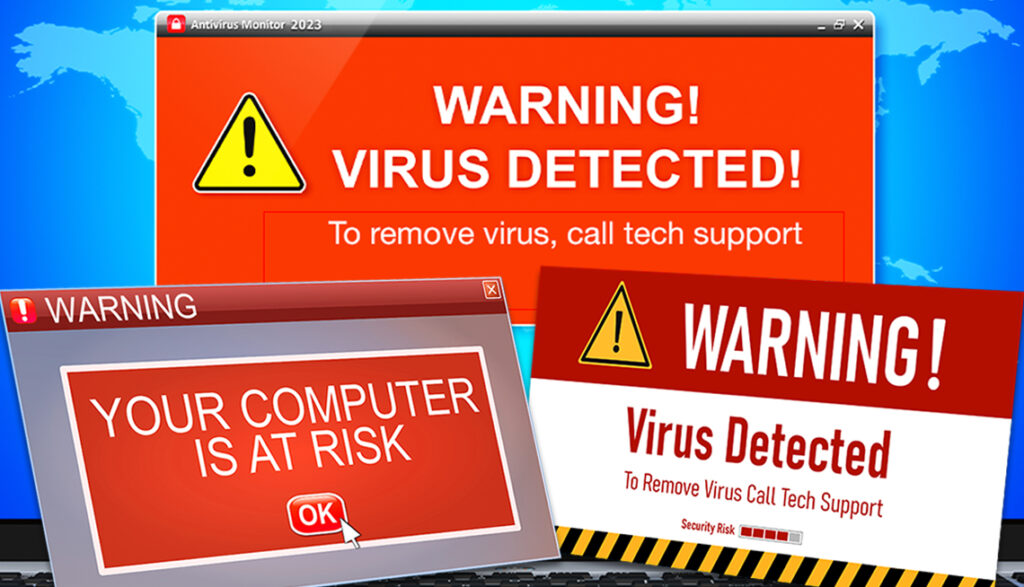
Tech support scams, where scammers pretend to be from a reputable company, such as Microsoft or Apple, and claim that your device has a problem that they can fix. They may ask you to give them remote access to your device, pay for their service, or download malware.
Some other types of scams are:
- Lottery or sweepstakes scams, where scammers claim that you have won a large amount of money or a prize, but you need to pay a fee or taxes to claim it.
- Charity scams, where scammers pretend to be from a genuine charity or cause and ask you to donate money or goods. They may use fake websites, emails, or phone calls to solicit your donations.

- Be wary of any phone call or text message that you are not expecting or that sounds too good or too bad to be true. Always hang up or ignore any robocall or text message that asks you to press a button, say a word, or follow a link. Do not answer or respond to any phone call or text message from an unknown or suspicious number or sender.
- Be careful of any phone call or text message that claims to be from a government agency, a law enforcement officer, a survey taker, a relative, a delivery person, or a well-known company. Always verify the caller’s or the sender’s identity and the authenticity of the request, and do not provide any information, money, or gift cards over the phone or by text. Do not trust any caller ID, document, or website that can be easily faked or spoofed.
- Be cautious of any app that you download or use on your phone or device. Always check the app’s reviews, ratings, permissions, and privacy policy, and do not install or use any app that you do not trust or that has negative or no feedback. Do not allow any app to access your contacts, messages, location, camera, microphone, or storage, unless you are sure that the app is safe and necessary.
- Be skeptical of any QR code that you scan or use on your phone or device. Always check the QR code’s destination, content, and purpose, and do not scan or use any QR code that you do not recognize or that has no clear explanation. Do not allow any QR code to access your device’s camera, microphone, or storage, unless you are sure that the QR code is safe and legitimate.
- Be careful of any email or message that asks you to click on a link, download an attachment, or provide your personal or financial information. Always verify the sender’s identity and the legitimacy of the request, and do not open or respond to any suspicious email or message.
- Be cautious of any token or smart contract that promises high returns or low risks. Always do your research and check the credibility and reputation of the token or smart contract, and the platform or exchange that supports it. Do not invest or trade with any token or smart contract that you do not understand or trust.
- Be skeptical of any image, video, or audio that seems too good or too bad to be true. Always check the source and the context of the image, video, or audio, and look for signs of manipulation, such as inconsistencies, distortions, or glitches. Do not believe or share any image, video, or audio that you cannot verify or that contradicts other reliable sources.
- Do your research before you respond to any offer, request, or message. Check the credibility and reputation of the source, and look for signs of fraud, such as spelling errors, poor grammar, or unrealistic claims.
- Never send money or personal information to someone you don’t know or trust, especially if they ask you to use untraceable methods, such as gift cards, wire transfers, or cryptocurrency.
- Be wary of any offer or request that sounds too good or too bad to be true, or that pressures you to act quickly or urgently.
- Contact the official organization or company directly, using their official website or phone number, if you have any doubts or questions about an offer, request, or message.
- Report any suspicious or fraudulent activity to the relevant authorities. You can also report it to the platform or service where you encountered the scam, such as the dating site, the social media site, or the online marketplace.
You think you have a story worth everyone’s time? SUBMIT A STORY and we will publish it.
Share this content:




Post Comment