Cybercriminals Abusing Cloudflare Tunnels to Evade Detection and Spread Malware
Cloudflare Tunnels, a legitimate service designed to provide secure access to internal networks, has become an unwitting accomplice in cybercrime. Cybercriminals are increasingly exploiting this technology to evade detection, distribute malware, and establish persistent command-and-control (C&C) channels. This article delves into the mechanics of this attack vector, its implications, and potential countermeasures.
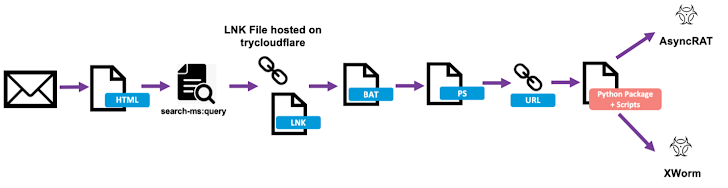
According to Proofpoint, on July 11, 2024, a cyberattack campaign targeting finance, manufacturing, and technology sectors leveraged Cloudflare tunnels to distribute AsyncRAT and Xworm malware.
How Cloudflare Tunnels Work
Before understanding the abuse, it’s essential to comprehend how Cloudflare Tunnels function. Essentially, they create encrypted tunnels between local networks and the Cloudflare network. This allows users to access internal resources remotely without exposing their IP addresses. While this is a valuable tool for legitimate use, it also offers significant advantages to malicious actors.
The Abuse of Cloudflare Tunnels
Cybercriminals are leveraging Cloudflare Tunnels in several ways:
- Malware Distribution: By creating temporary tunnels, attackers can host malicious payloads on compromised systems, making them accessible via seemingly legitimate Cloudflare subdomains. This obfuscates the true origin of the malware and makes it difficult for security solutions to detect.
- C&C Communication: Cloudflare Tunnels provide a stable and encrypted channel for C&C communication. This allows attackers to maintain persistent control over infected systems without fear of detection or interruption.
- Data Exfiltration: Sensitive data can be exfiltrated through Cloudflare Tunnels, bypassing traditional security measures. The encrypted traffic makes it challenging to identify and intercept data transfers.
Evading Detection
Cloudflare Tunnels offer several advantages to cybercriminals in evading detection:
- Dynamic Infrastructure: The ephemeral nature of Cloudflare Tunnels makes it difficult for security solutions to track and block malicious activity.
- Encrypted Traffic: The encrypted nature of the tunnels obscures the content of the communication, making it challenging to analyze for malicious indicators.
- Legitimate Service Abuse: Since Cloudflare Tunnels are a legitimate service, it’s harder for security systems to distinguish between legitimate and malicious use.
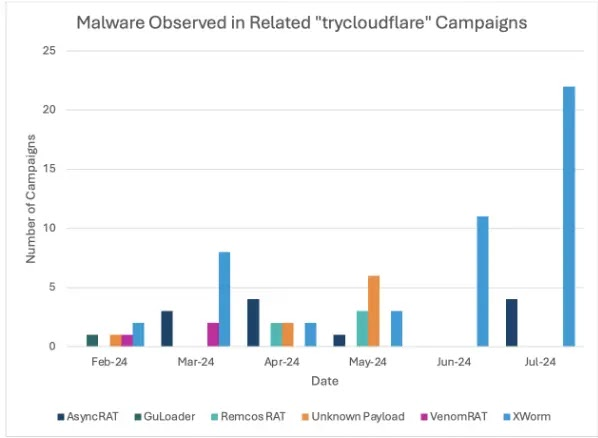
Impact and Countermeasures
The abuse of Cloudflare Tunnels has significant implications for organizations:
- Increased attack surface: The potential for malware distribution and C&C communication expands the attack surface.
- Data loss: Exfiltration of sensitive data can lead to financial losses, reputational damage, and legal consequences.
- Business disruption: Malware infections and data breaches can disrupt operations and impact productivity.
To mitigate these risks, organizations should implement the following countermeasures:
- Enhanced threat intelligence: Stay updated on emerging threats and tactics, including the abuse of Cloudflare Tunnels.
- Network segmentation: Isolate critical systems and data to limit the potential impact of a breach.
- Next-generation firewalls: Employ firewalls capable of inspecting encrypted traffic to detect malicious activity.
- User education: Train employees to recognize phishing attempts and avoid clicking on suspicious links.
- Incident response planning: Develop a comprehensive incident response plan to minimize damage in case of a breach.
Conclusion
The abuse of Cloudflare Tunnels by cybercriminals underscores the evolving nature of cyber threats. While Cloudflare has implemented measures to combat abuse, organizations must remain vigilant and adopt a layered security approach to protect against these attacks.
You think you have a story worth everyone’s time? SUBMIT A STORY and we will publish it
Share this content:




Post Comment