New Malware Masquerades as Palo Alto VPN Targeting Middle East Users
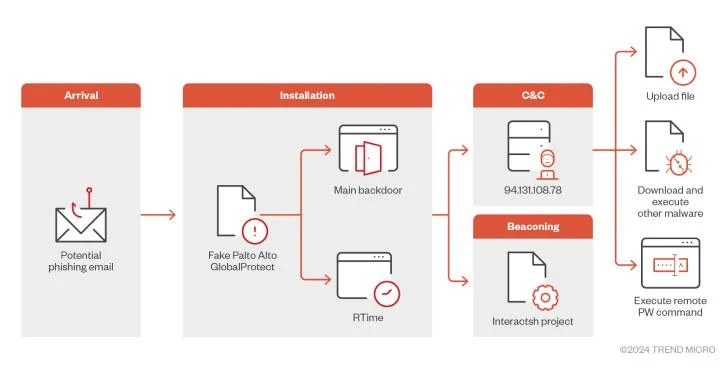
In a recent cyber threat landscape, a new malware variant has emerged, posing a significant risk to users in the Middle East. This malicious software, designed to steal sensitive data, is cleverly disguised as a legitimate Palo Alto Networks VPN client. The deceptive nature of this attack vector makes it particularly dangerous, as it leverages the trust users place in reputable cybersecurity brands.
Understanding the Threat
The newly discovered malware, codenamed “PaloAltoVPN,” is engineered to infiltrate systems by tricking users into downloading and installing a malicious version of the genuine Palo Alto Networks VPN client. Once executed, the malware establishes a backdoor, enabling attackers to gain unauthorized access to compromised devices.
Key Attack Tactics
- Phishing Campaigns: The attackers employ sophisticated phishing tactics to lure unsuspecting victims into downloading the malicious software. These campaigns often involve emails that appear to originate from legitimate sources, such as IT departments or cybersecurity firms, urging users to update their VPN clients.
- Social Engineering: The attackers may also leverage social engineering techniques to manipulate victims into clicking on malicious links or downloading attachments. This can include creating a sense of urgency or fear to pressure users into making hasty decisions.
Potential Consequences
- Data Exfiltration: The primary goal of the malware is to steal sensitive data, such as login credentials, financial information, and intellectual property. Once attackers gain access to compromised systems, they can exfiltrate this data for various malicious purposes.
- Network Compromise: The malware can also be used to compromise entire networks, allowing attackers to move laterally and target additional systems. This can lead to significant disruptions and financial losses.
Mitigation Strategies
- Verify Software Sources: Always verify the source of software downloads. Ensure that you obtain updates and patches directly from the official websites of reputable vendors.
- Be Wary of Phishing Attempts: Be cautious of unsolicited emails, especially those that contain urgent requests or attachments. Never click on suspicious links or download attachments from unknown sources.
- Use Strong Passwords: Employ strong, unique passwords for all your online accounts. Avoid using easily guessable information and consider using a password manager to help you manage your credentials securely.
- Keep Software Updated: Regularly update your operating system, applications, and security software to patch vulnerabilities that could be exploited by attackers.
- Implement Network Security Measures: Implement robust network security measures, such as firewalls, intrusion detection systems, and secure remote access protocols, to protect your systems from unauthorized access.
Conclusion
The emergence of the “PaloAltoVPN” malware highlights the ongoing threat posed by cybercriminals targeting users in the Middle East. By understanding the tactics employed by these attackers and taking proactive measures to protect your systems, you can significantly reduce your risk of falling victim to such malicious attacks. Stay vigilant, be informed, and prioritize cybersecurity best practices to safeguard your sensitive data and network infrastructure.
You think you have a story worth everyone’s time? SUBMIT A STORY and we will publish it
Share this content:




Post Comment