NIST Introduces Cybersecurity Framework 2.0 – A Quick Look!
The latest iteration of the Cybersecurity Framework from the US National Institute of Standards and Technology (NIST), version 2.0, underscores a heightened emphasis on governance and supply chain concerns.

With a renewed focus on these critical areas, the framework aims to bolster resilience and fortify defenses against evolving cyber threats. Additionally, Version 2.0 introduces an array of resources aimed at expediting the implementation process, empowering organizations to swiftly adopt and integrate the framework’s guidelines into their cybersecurity strategies.
Following two years of dedicated development, the US National Institute of Standards and Technology (NIST) has officially released the 2.0 version of its highly influential Cybersecurity Framework (CSF). Building upon the initial draft issued in September, the CSF 2.0 marks a pivotal shift in focus from safeguarding critical infrastructure, such as hospitals and power plants, to encompassing all organizations across diverse sectors.
This strategic pivot aligns with its inclusion in President Biden’s National Cybersecurity Strategy and various emerging government cybersecurity policy declarations. Notably, the framework has undergone a nomenclature adjustment, discarding its previous title, “Framework for Improving Critical Infrastructure Cybersecurity,” in favor of the more inclusive “NIST Cybersecurity Framework (CSF) 2.0” to better reflect its broadened applicability.
The latest iteration of the Cybersecurity Framework (CSF), version 2.0, represents a notable departure from its predecessors. Unlike the static nature of the original version in 2015 and its subsequent update in 2018, CSF 2.0 emerges as a dynamic set of resources tailored to guide the implementation process comprehensively. Under Secretary of Commerce for Standards and Technology and NIST Director Laurie E. Locascio emphasized this evolution, highlighting that CSF 2.0 transcends a single document, instead offering a flexible suite of resources.
Significant Enhancement: Introducing the “Govern” Function.
The pivotal addition of the Govern function marks a significant structural evolution within the Cybersecurity Framework (CSF). Serving as the foundational axis around which the existing functions of Identify, Protect, Detect, Respond, and Recover orbit, the introduction of this sixth function heralds a holistic approach to cybersecurity risk management.
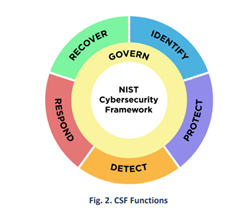
By aligning cybersecurity initiatives with broader enterprise risk management programs, the Govern function facilitates a seamless integration of security protocols into organizational strategies. Through its presentation of desired outcomes, or target states, the Govern function empowers organizations to effectively prioritize and achieve the objectives outlined across the spectrum of the remaining functions, thereby enhancing overall cybersecurity resilience.
Elevated Emphasis: The Heightened Role of the Supply Chain in CSF 2.0
The incorporation and expansion of supply chain risk management within CSF 2.0 represent a pivotal advancement from its predecessor, CSF 1.1. Under the umbrella of the Govern function, CSF 2.0 strategically consolidates and expands upon supply chain risk management outcomes. Acknowledging the intricate and interdependent nature of modern supply chains, the framework underscores the criticality of Cybersecurity Supply Chain Risk Management (C-SCRM) as a systematic approach to mitigating cybersecurity risks across supply chains. By aligning supply chain risk management with broader governance strategies, organizations are empowered to develop comprehensive response strategies, policies, processes, and procedures to address evolving threats effectively.
Despite this progress, challenges persist within the realm of supply chain security. According to industry experts, including O’Reilly, the integration of supply chain risk management into governance is just the initial stride in tackling this complex issue. With supply chain practices still largely fragmented and incomplete, there’s a recognized need for more robust top-down management to address the multifaceted challenges inherent in supply chain security. As such, while CSF 2.0 represents a significant step forward, further efforts are imperative to comprehensively manage the complexities of the modern supply chain landscape.
Enhancements in CSF 2.0: Updated References, Quick Start Guides, and Enhanced Resource Integration
The latest iteration of the Cybersecurity Framework (CSF) introduces updated informative references, encompassing existing standards, guidelines, and frameworks. These references serve to elucidate the technical intricacies and procedural steps outlined within the CSF, offering invaluable insight into the implementation process for organizations.
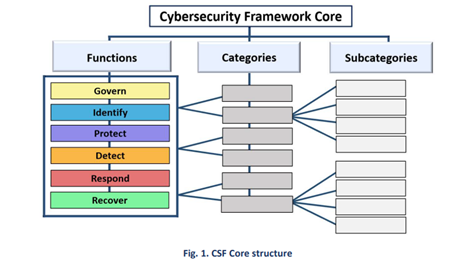
With a focus on operationalizing the framework’s 106 subcategories, which are clustered under 23 categories, this enhanced guidance facilitates a deeper understanding of cybersecurity best practices. Organized within the framework’s major functions, these references empower organizations to navigate and implement the CSF effectively, bolstering their cybersecurity resilience in an ever-evolving threat landscape.
To improve on potential adoption difficulties posed by the CSF, NIST incorporated into the 2.0 version a series of quick-start guides on several topics, including how to create CSF profiles and tiers and, notably, how to begin managing supply chain security risks and create community profiles to allow communities that share a common interest to describe consensus points of view.
To provide even more practical guidance on how to implement the framework, CSF 2.0 also offers implementation examples. These implementation examples (below) represent NIST’s effort to phrase the passively written outcomes into more active actionable steps organizations can take to adopt the framework.
Since the framework’s inception, NIST has taken care not to prescribe any particular steps organizations should take, given that every organization has unique technical and resource configurations. Instead, NIST has referred to outcomes, which some argue offer little practical guidance on what specific actions organizations should take.
NIST resources that deal with ERM, and ICT risk management programs are:
- SP 800-221, Enterprise Impact of Information and Communications Technology Risk: Governing and Managing ICT Risk Programs Within an Enterprise Risk Portfolio
- SP 800-221A, Information and Communications Technology (ICT) Risk Outcomes: Integrating ICT Risk Management Programs with the Enterprise Risk Portfolio
- SP 800-37, Risk Management Framework for Information Systems and Organizations
- SP 800-30, and Guide for Conducting Risk Assessments from the NIST Risk Management Framework (RMF)
Remember, cybersecurity is crucial in today’s interconnected world, and the CSF 2.0 serves as a valuable tool for organizations to enhance their security posture.
You think you have a story worth everyone’s time? SUBMIT A STORY and we will publish it.
Share this content:




Post Comment