The Rise of Red CryptoApp: A New Threat has emerged.
Red CryptoApp, a new ransomware group, emerged in March 2024. Unlike other ransomware groups, Red CryptoApp didn’t use a vanity Onion domain for their data leak site (DLS), which first appeared on March 29, 2024, under the title “Wall of Shame”. This group likely began to target its victims in mid-February 2024.
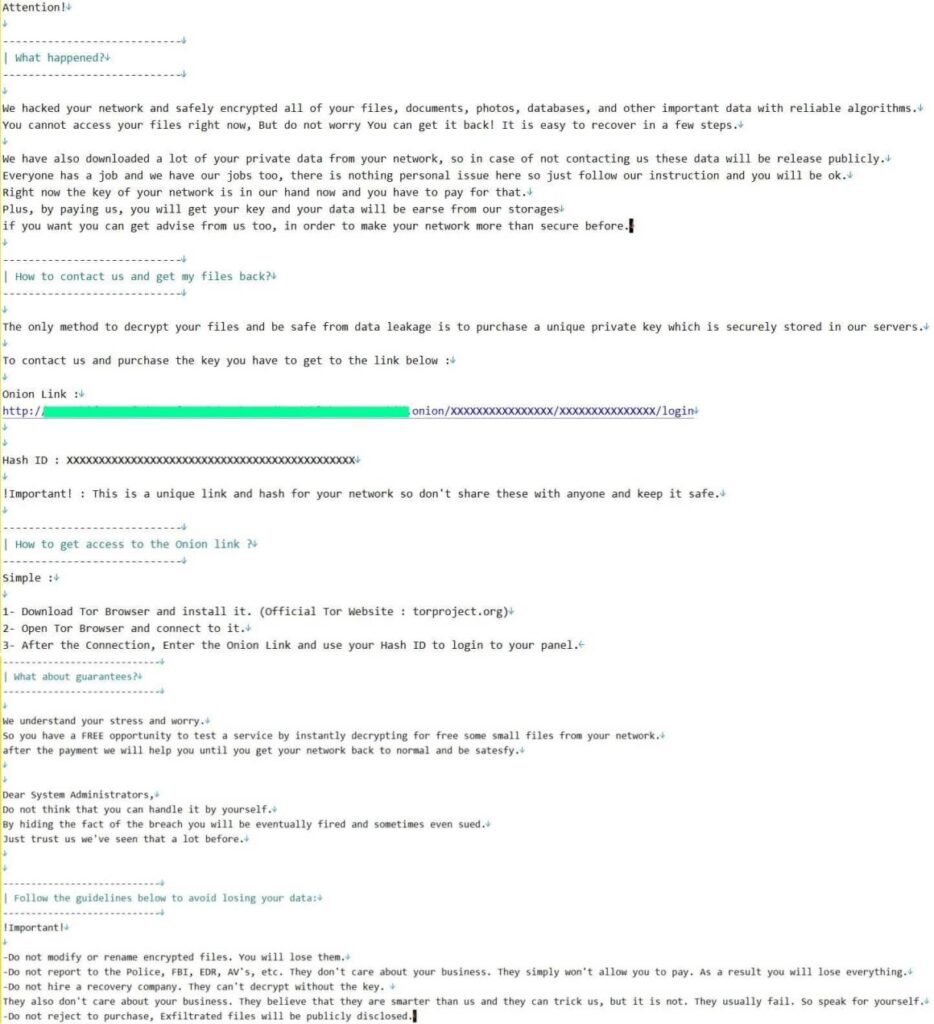
Modus Operandi of Red CryptoApp
Once a system is infected, all files are appended with a .REDCryptoApp extension. The group provides victims with a unique TOR URL to negotiate with them. When navigating to this unique URL, victims are prompted to provide their “Hash” (a unique ID for each victim) and solve a captcha to log into the chat window.
Targeted Countries and Industries
At the time of writing, the United States was the most targeted country, with five total victims. Other targeted countries include Denmark, India, Spain, Italy, Singapore, and Canada. The most targeted industries are software and manufacturing, with other sectors such as education, construction, hospitality, and IT also being targeted.
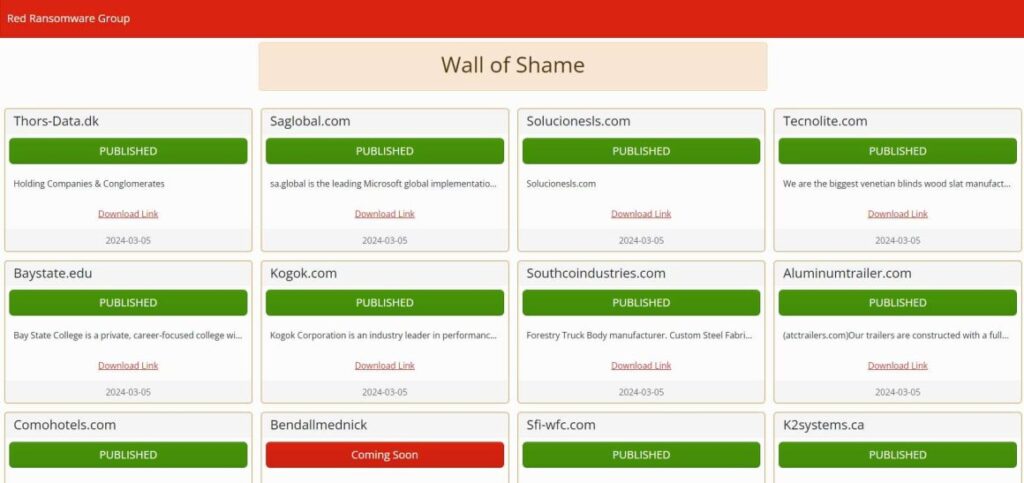
Technical Details
The Red CryptoApp group maintains two TOR domains. One is dedicated to hosting leaked victim data, and the other hosts the breached data of the 11 victims. The group’s ransom note is dated February 18, 2024, indicating that they likely started their operations in early 2024.
Protection Against Red CryptoApp
To protect against ransomware attacks like Red CryptoApp, organizations can take several steps. Regularly updating software is crucial, as ransomware often exploits vulnerabilities in outdated software. Protecting backups is another important step. Using offline storage, immutable storage, or out-of-band steps (like multifactor authentication or PIN) before modifying or erasing online backups can safeguard against deliberate erasure and encryption.
In conclusion, the emergence of Red CryptoApp is showing the evolving threat landscape of ransomware. Organizations must stay vigilant and adopt robust security measures to protect themselves against such threats.
You think you have a story worth everyone’s time? SUBMIT A STORY and we will publish it.
Share this content:




Post Comment